Securing Networks with Cisco Firepower Threat Defense (FIREPOWER200)
- Overview of technology
- Next Generation Firewall Security
- Types of Firewalls
- Routing in FTD
- Next Generation IPS
- IDS vs IPS
- Firepower Components and Features
- Firepower System
- Firepower Features
- Firepower Automation
- Firepower Components
- Firepower Management Center
- Firepower Device
- Firepower Naming Conventions
- Firepower Platforms
- Firepower Stacking
- Firepower Threat Defense
- Unified Access Control Policies
- High-level Feature Comparison
- Firepower 9300 and 4100 Details
- Firepower Management Center
- Firepower Management Center
- FMC Basics
- How FMC works
- FMC Management
- FMC Limits
- FMC GUI
- FMC GUI Menus
- FMC Analysis Menu
- FMC Policies Menu
- FMC Devices Menu
- FMC Domain Management
- How to Create FMC Domains
- Firepower Licensing
- Smart Licensing
- Cisco Firepower System Configurations
- FTD Device Registration
- FTD Device Configuration
- FMC Configuration
- FTD Device Properties
- FTD Interfaces
- FTD Modes
- FMC Policies Basics
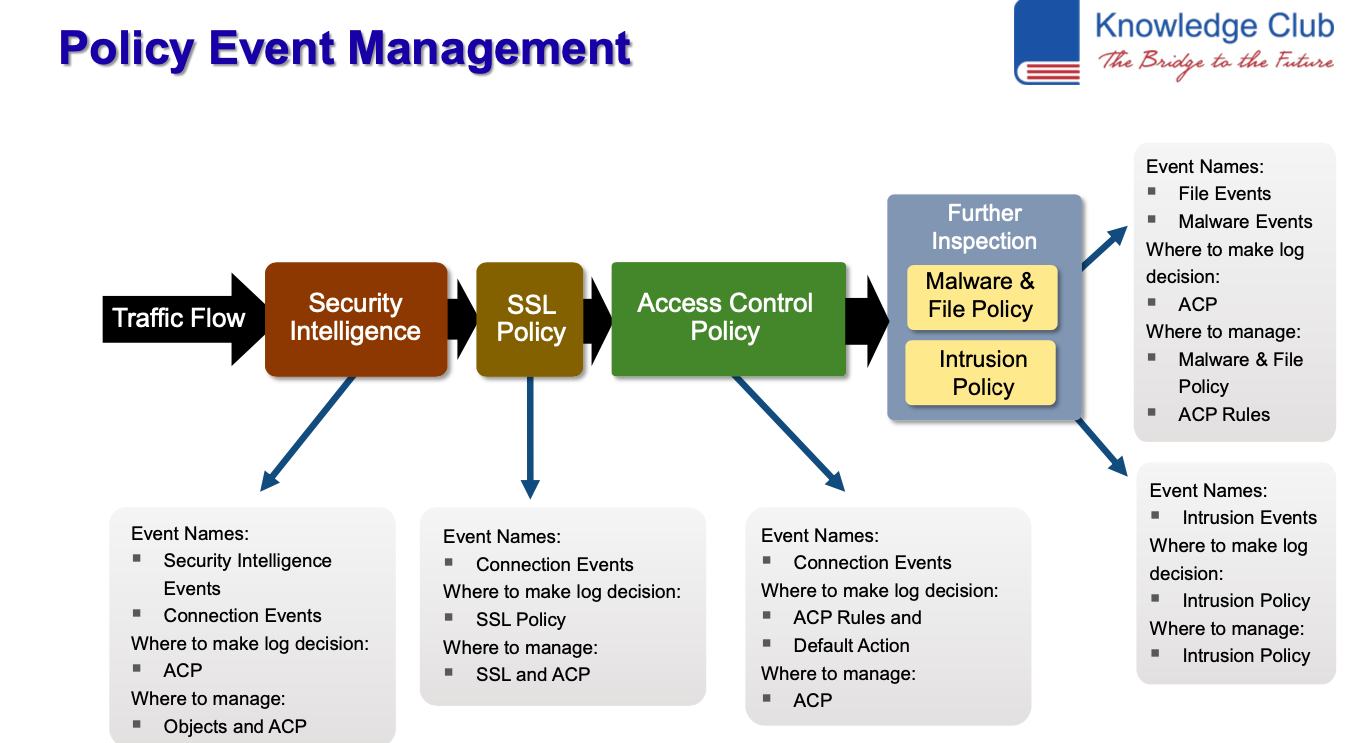
- Firepower Policy Flow
- Deployment
- Firepower High Availability
- Firepower Management Center HA
- 7000 and 8000 HA
- Firepower Threat Defense HA
- NAT Policy Configuration
- NAT Policy Configuration
- How NAT Works
- NAT Types
- Configuring NAT with FMC
- NAT Rules
- NAT Auto NAT Rules
- NAT PAT pool
- Advanced NAT
- NAT Verification
- NAT Examples
- QoS Policy Configuration
- How QoS Works
- How to Create QoS Policy
- QoS Policy Rules
- QoS Examples
- FlexConfig Policies
- FlexConfig Policy Overview
- Template Scripts
- Customizing Device Configuration
- Firepower Discovery
- Network Discovery Components
- Fingerprinting Hosts
- How it works
- Discovery Modes
- Passive Detection
- Active Detection for Hosts
- Host Identity
- Identity Workflow
- Conflict Workflow
- Discovery Policies
- Network Discovery Policy
- Network Discovery Rules
- Rule Actions
- Host Limits
- Discovery of Users
- User Limits
- Identity Sources
- Captive Portal
- User Identity Configuration
- Identity Policy
- Objects
- Object Basics
- Object Groups
- Overrides
- ACP Object Relationship
- General Objects
- Advanced Objects
- Variables
- Prefilter Policies
- Introduction to Prefiltering
- Prefiltering vs Access Control
- Configuring Prefiltering
- Access Control Policy
- ACP Components
- ACP Rules
- ACP Default Action
- Rule Action – Block
- Rule Action – Monitor
- Rule Action – Trust
- Rule Action – Allow
- ACP Inspection Options
- Logging Options
- ACP Advanced Settings
- ACP Inheritance
- Security Intelligence
- Security Intelligence Overview
- SI Whitelists and Blacklists
- SI Objects
- SI Feeds
- Feed Categories
- List Objects
- SI Deployment
- File and Malware Policy
- File Identification SHA-256
- File-Type Detection
- File Policy Rules
- File Policy Basics
- File Types
- Advanced Options
- Advanced Malware Protection
- File Dispositions
- AMP Cloud
- AMP Architecture
- AMP Advanced Options
- AMP Integration
- Next Generation Intrusion Prevention
- Intrusion Prevention Basics
- Rules
- Rule Examples
- Snort
- Talos
- Variables
- Intrusion Policy
- Network Analysis Policy
- Traffic Flow for Intrusion Policy
- Components
- Policy Layers
- Shared Policy Layers
- Creating New Intrusion Policy
- Intrusion Policy Configuration
- Intrusion Policy Rules
- Rule Options
- Firepower Recommendations
- Network Analysis Policy
- Preprocessor Technology
- Preprocessor Flow
- Preprocessor Rules
- Network Policy Settings
- Adaptive Profiles
- Adaptive Profile Configuration
- SSL Policy
- Anatomy of SSL Sessions
- Firepower SSL Decryption
- Firepower SSL Architecture
- Decrypt Resign
- Decrypt Known Key
- SSL Policy
- SSL Policy Settings
- SSL Policy Rules
- SSL Policy Default Action
- Applying SSL Policy
- VPN Deployments
- VPN Overview
- VPN Types
- VPN Basics
- Licensing
- Firepower Threat Defense Site-to-Site VPN
- Firepower Threat Defense Remote Access
- VPNs
- Correlation Policies
- Responses
- Remediation
- Custom Remediation Modules
- Correlation Policy Rules
- How to Create Policy Rules
- Whitelists
- Traffic Profiles
- Correlation Policy
- Analysis
- Event Basics
- FMC Analysis
- FMC Database
- eStreamer
- Analysis Search
- Workflows
- Security Intelligent Events
- File and Malware Events
- Impact Flags
- Indication of Compromise
- Analysis Tools
- Reporting
- System Administration
- System Configuration
- FMC Configuration Settings
- Health Monitoring
- Health Policy
- Firepower Updates
- User Account Management
- Multidomain Deployments
Başvurunuz kayıt numarası ile alınmıştır.
Talep Formu
| Adınız ve Soyadınız | |
| E-Posta Adresiniz | |
| Telefon Numarası | |
| Çalıştığınız Yer | |
| Okuduğunuz Okul | |
| Mesajınız |
Aktarılıyor...Dosya hazırlanıyor